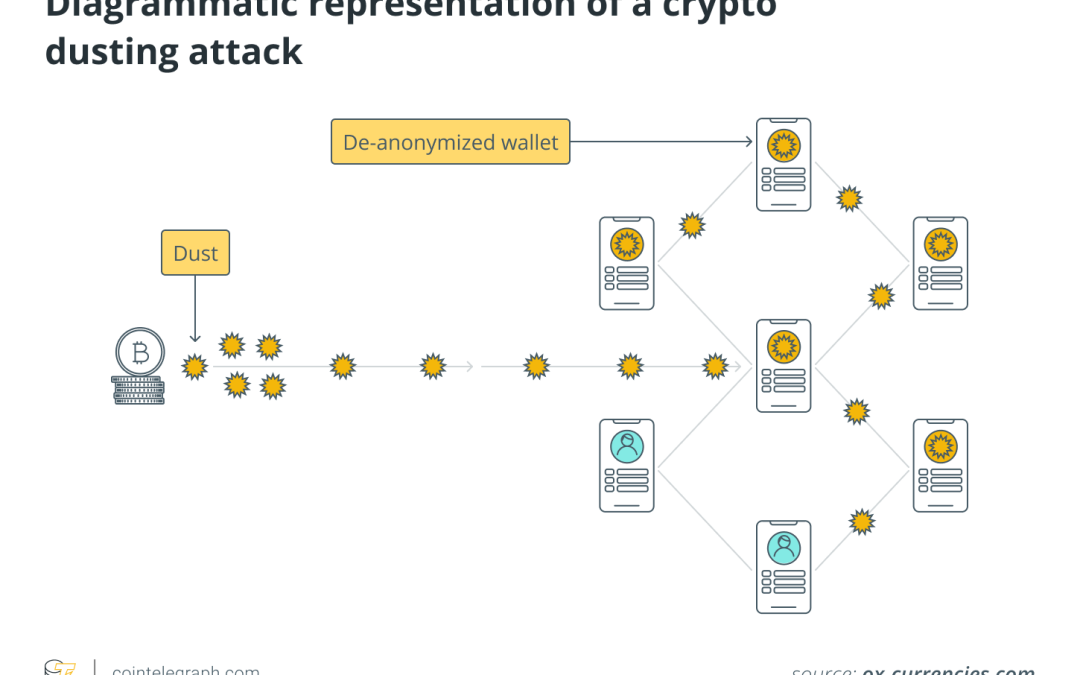
Malicious actors rely on the fact that cryptocurrency users don’t even realize they received tiny amounts of cryptocurrencies in their wallet addresses.
Of the way blockchains work, with their transparency and traceability, it is possible to track down transaction movements that may lead to the identification of wallet owners. For a dust attack to be effective, the owner of the wallet must combine the crypto dust with other funds in the same wallet and use it for other transactions.
By including a small amount of cryptocurrency in other transactions, the target of the attack may inadvertently and unknowingly send the dust to an off-blockchain centralized organization. As the centralized platform must comply with Know Your Customer (KYC) regulations, it will store the personal data of the victim, who may become vulnerable to phishing, cyberextortion threats, blackmailing and other targeted hacks off the blockchain aimed at stealing sensitive information.
The cryptocurrency addresses that are more vulnerable to dusting attacks are the UTXO-based addresses used in various blockchains, mainly Bitcoin, Litecoin and Dash, because they all generate a new address for each change remaining from transactions. UTXO prevents double-spending and is an unspent transaction output that remains after a transaction is executed and can be used as input on another transaction.
It’s like the change we receive from a merchant when we spend $9.59, for example, after giving a $10 bill. Just like that tiny change can be used in other money transactions later, the crypto dust from multiple addresses can be spent in other transactions. By detecting the origins of funds from the dust attack transaction, the attackers can use advanced technological tools to trace a thread to determine the victim’s identity.