There are several ways to add layers of anonymity to bitcoin cash (BCH) transactions such as using a VPN or shuffling coins with mixers. One way to anonymize when using the BCH chain is by utilizing free Tor software while transacting online. This way, internet traffic is encrypted and routed through nodes throughout the overlay network. Tor won’t hide the transaction’s path, but bitcoiners using the Tor network can make it extremely hard for investigators to pinpoint their IP address and geolocation.
Also read: How to Use a VPN in the EU to Access the Uncensored Web
The Overlay Network Known as Tor
 When Satoshi Nakamoto launched the Bitcoin network, the creator did not make the protocol anonymous. The network is not private and all the transactions broadcast over the network are available to see by anyone with a copy of the blockchain. However, the technology is pseudo-anonymous and when transacting with a cryptocurrency like bitcoin cash, users can add a few levels of privacy to obfuscate BCH transactions. One privacy method cryptocurrency proponents use is the Tor protocol, an overlay network consisting of thousands of nodes that conceal a user’s location. If a person were to send a bitcoin cash transaction using the Tor network it would help encrypt and route the web traffic, which essentially hides the user’s location and internet provider (IP).
When Satoshi Nakamoto launched the Bitcoin network, the creator did not make the protocol anonymous. The network is not private and all the transactions broadcast over the network are available to see by anyone with a copy of the blockchain. However, the technology is pseudo-anonymous and when transacting with a cryptocurrency like bitcoin cash, users can add a few levels of privacy to obfuscate BCH transactions. One privacy method cryptocurrency proponents use is the Tor protocol, an overlay network consisting of thousands of nodes that conceal a user’s location. If a person were to send a bitcoin cash transaction using the Tor network it would help encrypt and route the web traffic, which essentially hides the user’s location and internet provider (IP).
People can download the Tor software for Windows, Mac, and GNU/Linux from the official website. Tor is about 64MB in size and downloads quickly from the server depending on your internet speed. The program can run immediately after the install but it can also be installed to a USB flash drive. Tor comes with its own web browser that protects anonymity when it’s used to surf the internet.

VPN, Tor and Tumble
Most of the time when people are using Tor to conceal the original location of BCH transactions, individuals will create a bitcoin cash wallet while using the Tor network. Additionally, they can use a virtual private network (VPN) to further bury their internet traffic. Both Tor and a VPN will help confuse online investigators looking for the exact location of a user who sent the transaction. Tor will not conceal the original BCH addresses or destinations, as blockchain surveillance can follow these inputs and outputs. A user who wants to overcome this anonymity hurdle has to use a cryptocurrency tumbler or mixer to hide the fund’s original derivation and paths going forward. If a person uses Tor coupled with a VPN and then uses a bitcoin cash tumbler as well, the chances of the owner being found are much slimmer.

Running a Bitcoin Cash Full Node With the Tor Network
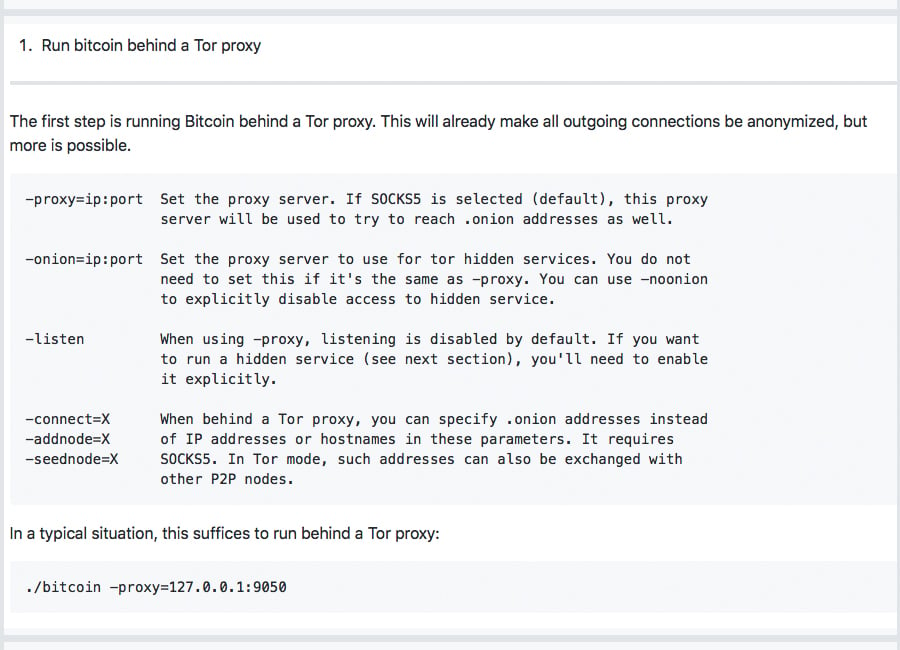
 There’s also a way that BCH full node operators can hide their transaction originations over the Tor network. For instance, a user can download the Bitcoin ABC client or another BCH implementation and route traffic through the Tor network instead of having it stem from a real IP address. As long as the user has a Tor proxy running on port 9150 they can send and receive BCH using a full node client in a fairly anonymous manner.
There’s also a way that BCH full node operators can hide their transaction originations over the Tor network. For instance, a user can download the Bitcoin ABC client or another BCH implementation and route traffic through the Tor network instead of having it stem from a real IP address. As long as the user has a Tor proxy running on port 9150 they can send and receive BCH using a full node client in a fairly anonymous manner.
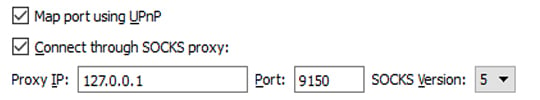
In order to configure the Tor browser to work with a BCH full node client, the Tor SOCKS proxy host must be the same. To find this in the Tor browser, simply select the advanced network settings in the tools section and make sure the configuration is set to 127.0.0.1: 9150. After checking the Tor configuration, the Bitcoin ABC client or another BCH implementation needs to be set to 127.0.0.1: 9150 as well. In the full node client’s user interface (UI), look for the network tab in the settings section and configure the BCH implementation to 127.0.0.1:9150.
Your Sovereign Right to Use Privacy Protocols
There are additional steps to take a BCH full node implementation further down the road of privacy by binding the address using the Tor proxy. The user can study and execute a variety of methods so all clearnet connections are unable to connect and view the incoming and outgoing traffic. The Tor protocol, VPNs, and tumblers are great methods to anonymize bitcoin cash transactions, but none of them are 100 percent full-proof. They do help confuse blockchain surveillance, though, if you are concerned with onlookers viewing your funds. Moreover, anyone can use these protocols to make themselves anonymous. While there’s a misconception that only criminals use these tools, that’s really not the case. Privacy is extremely important to a lot of people in this world, especially when it comes to money. Just like using the BCH protocol, every individual on this planet has the sovereign right to use a VPN, Tor, and even mixing services.
What do you think about using Tor while sending bitcoin cash transactions? Let us know what you think about the Tor project in the comments section below.
Disclaimer: Walkthrough editorials are intended for informational purposes only. There are multiple security risks and methods that are ultimately made by the decisions of the user. There are various steps mentioned in reviews and guides and some of them are optional. Bitcoin.com and the author are not responsible for any losses, mistakes, skipped steps or security measures not taken, as the ultimate decision-making process to do any of these things is solely the reader’s responsibility. For good measure always cross-reference guides with other walkthroughs found online.
Images via Tor, Pixabay, Github, Fossbytes, and Electron Cash.
Need to calculate your bitcoin holdings? Check our tools section.
The post Send Bitcoin Cash Over the Web in a Private Fashion Using Tor appeared first on Bitcoin News.