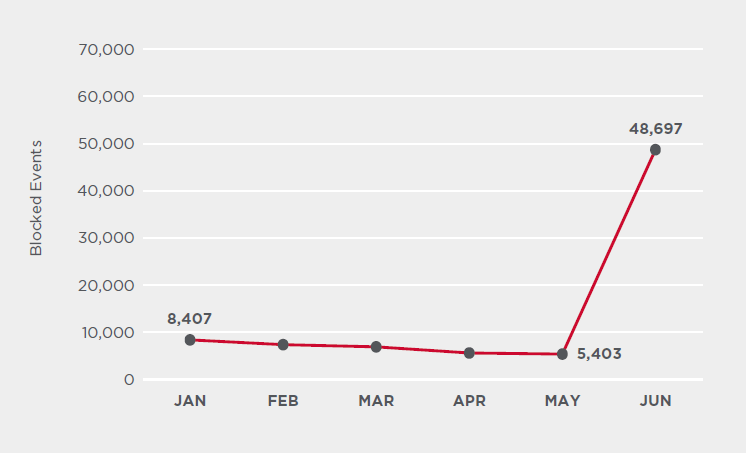
The spike has been seen in the aftermath of Black Thursday in March this year as lockdowns across the world began
According to recently published research by US-based security vendor Symantec, cryptojacking may be making a comeback. The study showed a significant and sudden spike in the number of detected cryptojacking events. This online threat poses a huge risk to the crypto users’ community and other netizens at large.
Cryptojacking is the act of compromising web browsers, and can sometimes extend to computers, mobile devices and even network servers. The motive behind these malicious attacks is profit by using up all available computer resources to mine crypto. The attacks are designed to stay hidden so that users don’t realise what is happening.
There were initial reports of this browser-based cryptocurrency mining form making a comeback in June this year. Symantec, through the Threat Landscape Trends report for the second quarter of the year, revealed a 163% spike in cryptojacking detections compared to other quarters.
Cryptojacking history
This spike is very atypical considering most security experts flagged cryptojacking to be a long-dead method of cyber-attack. Cryptojacking incidents were prevalent in the early days of crypto mining and peaked between September 2017 and March 2019. This happened at about the same time when Coinhive was operational.
The German-based web service was initially launched as an alternative site monetisation scheme, but later became associated with cybercrimes. Coinhive enabled crypto users to mine Monero by incorporating a JavaScript library string [coinhive.js] into the website’s source code.
After the shutdown of the mining script maker, cryptojacking cases had been in decline.
Is it time to start worrying?
Symantec had detected only a few events of cryptojacking in the months leading up to the spike. The reason behind this spike is yet to be known, but most security experts speculate it was due to a router botnet.
This happens when malware groups illegally access home routers and reconfigure DNS settings to hijack legitimate traffic. The hacked routers serve as proxies, and in a few cases, they’re used to launch attacks such as DDoS.
Security experts believe that some cybercriminals try to monetise their router botnets by running cryptojacking scripts. These scripts are essentially modified versions of coinhive.js that are updated to work even without using Coinhive. That said, experts don’t envision a full cryptojacking comeback in spite of the recorded spike.
The post Cryptojacking has seen a recent spike: Symantec reports appeared first on Coin Journal.